Easily reduce and eliminate low-value data
Are you challenged by:
- Data overload that causes noise and inefficiency
- High data cost of storing, processing, and handling large volumes of data
- Vendor lock-in with reliance on expensive tools and data costs
- Unexpected data growth from custom applications leading to high observability costs.
Mezmo can help you optimize your data to reduce costs by as much as 80%.
As the complexity of your applications and systems grows, so does the volume and complexity of the telemetry data they produce. Simply understanding what data is being sent to your observability and storage solutions is almost impossible, let alone whether it is appropriately structured and formatted for its intended use.
Solution:
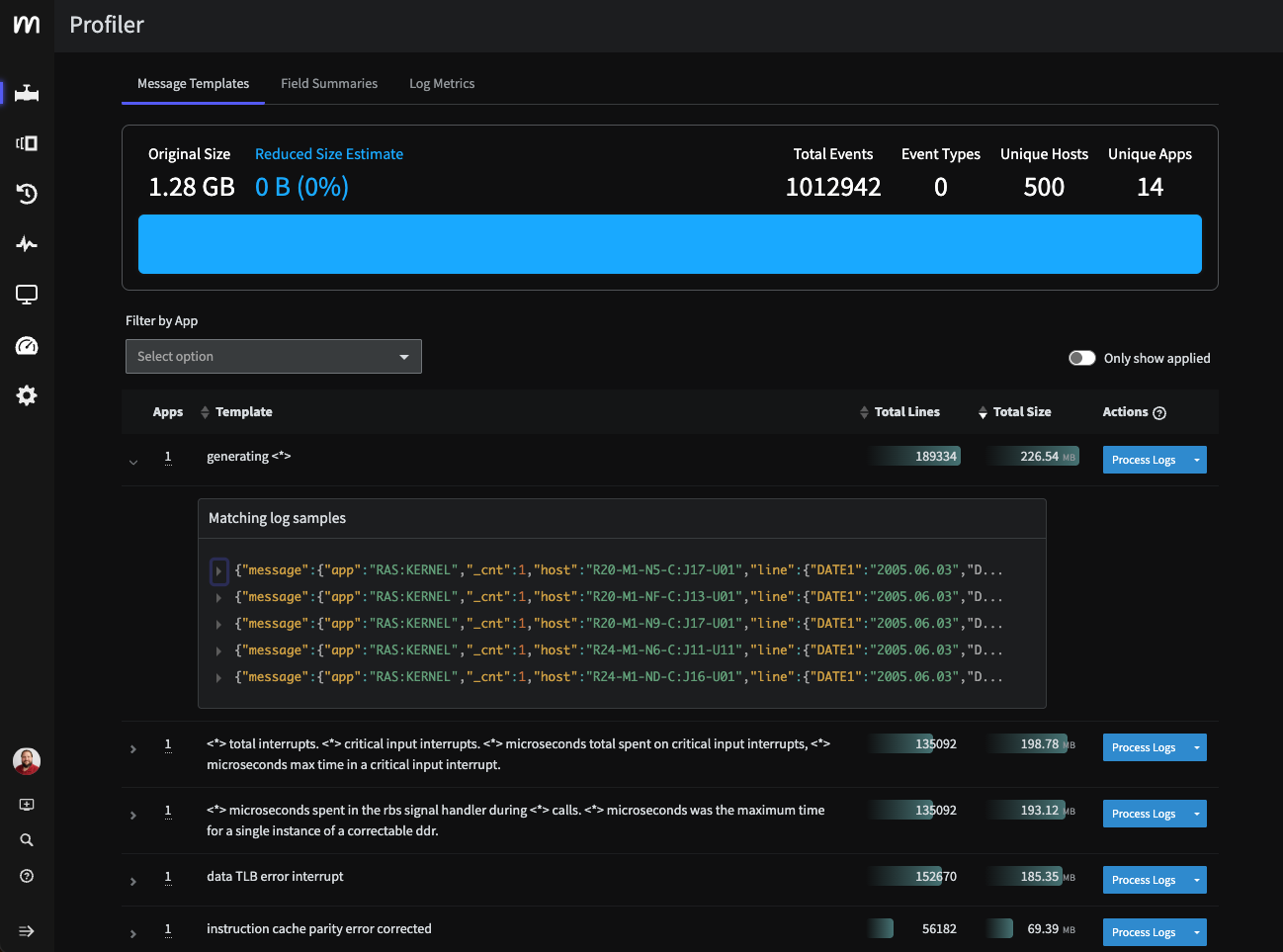
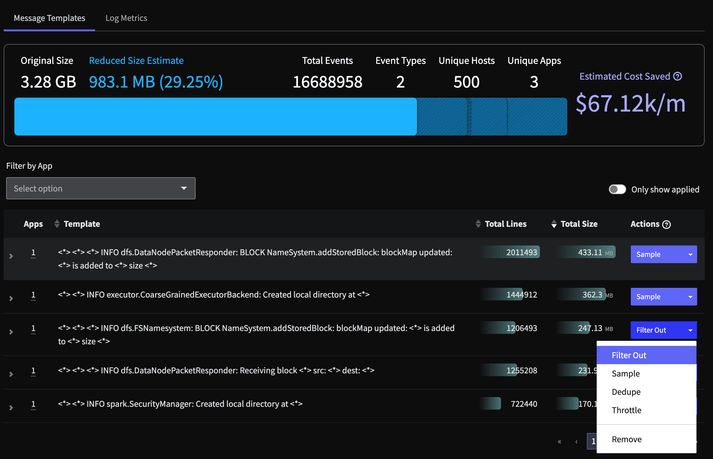
With features of Mezmo Active Telemetry Platform, like data profiling, you can gain an in-depth understanding of your data. At the same time, pipeline processors enable you to separate the signal from the noise, and make sure your data is optimized to provide exactly the information you need.
Key capabilities for log volume reduction
Remove low-value logs (DEBUG/INFO) to reduce noise and manage costs effectively. Learn more about supported processors.
Decide what stays hot, what moves to cold storage (S3, Azure Blob, GCP), or gets dropped. Learn more about supported destinations.
Stream telemetry data in real-time and replay buffered events for instant incident investigation without waiting for indexing or storage delays.
Continuously analyze telemetry patterns to identify high-volume, low-value data streams and provide actionable recommendations for cost optimization. Learn how to use data profiling.
Automatically adapt pipeline behavior based on real-time conditions, scaling processing capacity and adjusting sampling rates to maintain performance during traffic spikes.
Enhance telemetry data with contextual metadata from external sources, standardize formats, and add business context to improve observability and enable better analysis.
Monitor and control metric cardinality in real-time to prevent exponential cost increases from high-cardinality tags while preserving essential dimensional data.
Real-world use cases for Active Telemetry
reduction
"Mezmo helped us reduce our overall telemetry data volume by 50% by filtering and parsing data to ensure we only indexed the fields we actually needed."
— Netlink Voice
"Teams using Mezmo consistently reduce mean time to resolution by 30-50% through cleaner, more relevant data feeding into their observability platform."
— Platform Engineering Team
"Using Data Profiler, we discovered we were sending massive amounts of verbose health check logs. Mezmo helped us create cost metrics and optimize our pipeline."
— Schier Engineering
Explore more
Stop paying to store noise
Start capturing signals
- ✔ Schedule a 30-minute session
- ✔ No commitment required
- ✔ Free trial available

